
Firewall as a Service
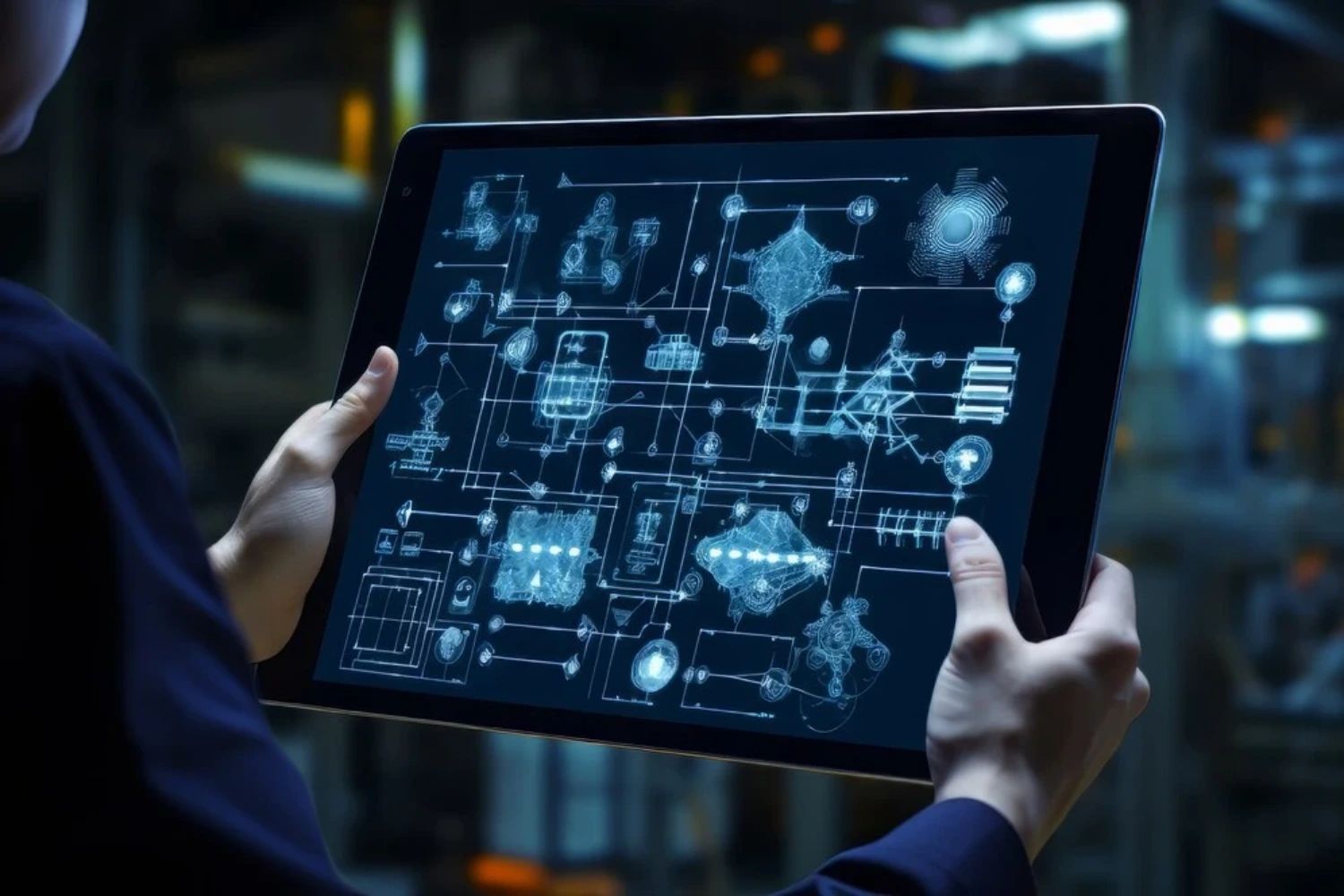
Firewall as a Service (FWaaS) is a cloud-based firewall solution that provides network security services to businesses without the need for physical hardware. Instead of deploying and managing on-premises firewall appliances, users can leverage FWaaS to secure their network traffic and applications in the cloud.
Pi Cloud offers a comprehensive Firewall as a Service (FWaaS) powered by Palo Alto Networks, a leader in cybersecurity. This service provides advanced security features to protect your digital assets and ensure robust defence against cyber threats. It is a cloud-based security solution that provides firewall functionality. It enables customers to protect their networks from unauthorized access and cyber threats while leveraging the scalability and flexibility of services.
Key Features

Advanced Real Time Threat Protection
- Advanced Threat Detection to identify and mitigate potential threats in real time.
- Prevention of malware, ransomware, and phishing attacks.
Application Control
- Detailed visibility and control over applications, users, and content.
- Granular policies to manage and restrict application usage.

Intrusion Detection & Prevention System (IPS/IDS)
- Proactive detection and prevention of network-based threats.
- Signature-based and anomaly-based threat detection.
URL Filtering
- Blocking of malicious websites and phishing sites.
- Customizable URL filtering policies to control web access.
Virtual Private Network (VPN)
- Secure remote access for employees through IPsec and SSL VPNs.
- Ensuring data confidentiality and integrity over public networks.

High Availability
- Redundant infrastructure to ensure continuous security operations.
- Automatic failover capabilities to minimize downtime.
Scalability
- Flexible scaling options to accommodate customers business growth.
- Easily adjusts to the changing needs of an organization.
- Pay-as-you-grow model to optimize costs.
- Can handle varying amounts of traffic without performance degradation.
Centralized Management
- Unified management console for streamlined security operations.
- Simplified policy management and reporting.
- It operates in the cloud, allowing for remote management and monitoring.
- Eliminates the need for on-premises hardware firewall.
Benefits
Enhanced Security
Protects against sophisticated cyber threats, ensuring sensitive data and network security.
Operational Efficiency
Minimizes the operational burden on IT teams by automating many security processes.
Flexibility
Adapts to various business sizes and needs, making it suitable for both small businesses and large enterprises.
Cost-Effective
Reduces significant upfront capital expenditure to customers on physical hardware and yearly maintenance.
Compliance
Helps meet regulatory requirements and industry standards for data protection.
FWaaS is an effective, scalable, and cost-efficient solution for organizations looking to enhance their network security without the complexities of traditional firewall management. By leveraging the power of the cloud based solution, businesses can protect their assets from evolving cyber threats while focusing on their core business operations.
Contact Pi Cloud to learn more about how Palo Alto Firewall as a Service can enhance your organization's security posture. Our team of experts is ready to assist you in customizing a solution that meets your specific needs.

